Byobu is a Japanese term for decorative, multi-panel screens that serve as folding room dividers. Source: http://byobu.co/about.html
As part of our penetration testing engagements, Alpine Security uses many of the command line tools that come with Kali Linux. We have several Kali systems we use with fixed IP addresses so that we can tell our customers which IPs the attacks will be coming from. This means that we end up doing many Secure Shell (SSH) sessions to these systems, many of which will be executing long-running processes. If we lose the SSH connection because of a network drop, the session executing the long-running process will die as well. There are ways to send processes to the background and log their output (such as using nohup), but there are more convenient ways to keep multiple sessions running, even when the SSH session that launched them dies.
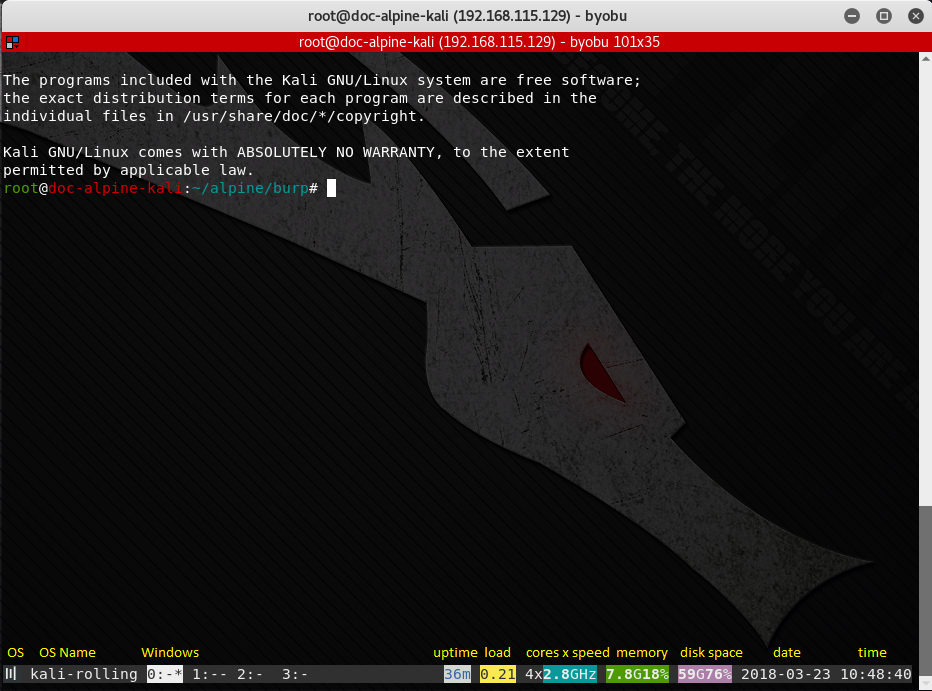
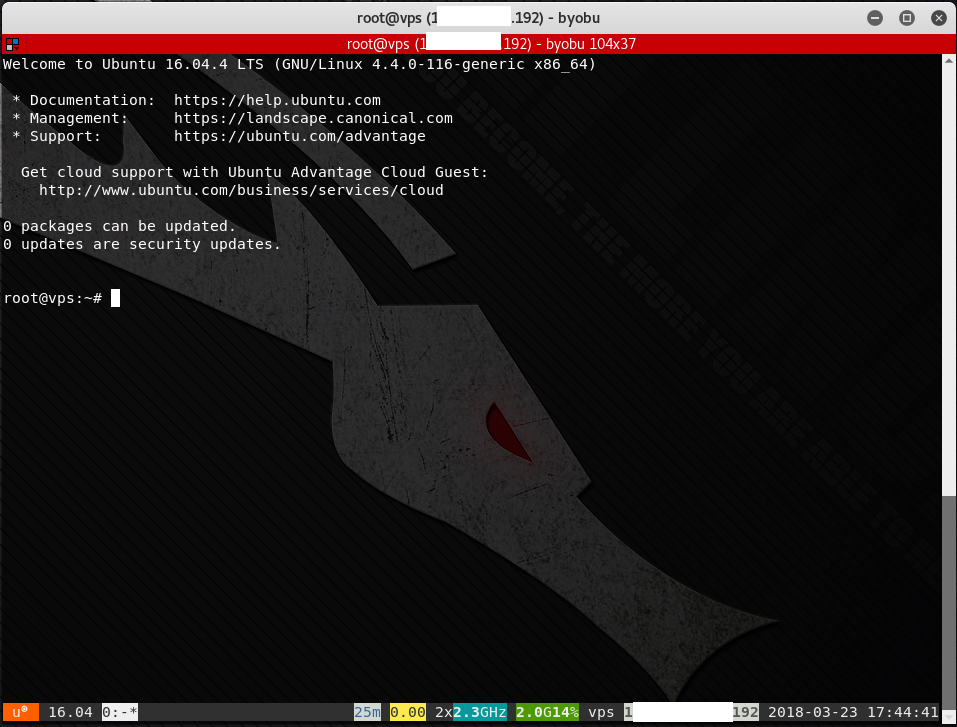
There are many terminal multiplexer programs available that allow sessions to live on after an SSH disconnect. Two of the most popular in Linux are GNU Screen and tmux. My personal favorite is byobu (after the Japanese folding screen). To run byobu, simply type “byobu” in the terminal window. The screenshot shows what byobu looks like. Along with the Message of the Day (/etc/motd) being displayed in the first window, a status bar appears at the bottom of the terminal window. The text in yellow above the status bar are labels that I added for illustrative purposes.
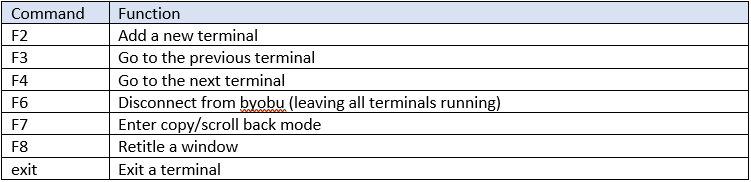
Some helpful commands are shown in the table below:
If you run byobu with no command line arguments, you will attach to the default session, called “byobu”. All users logged into the same session will be able to type commands and see the results in the session. This is actually a way for multiple users to watch what is going on in a terminal window. But what if each user wants his or her own session? You can specify a session name as follows:
byobu new -s [session-name]
Then any terminals created in that session will only be seen by a user who is attached to that session. To select a names session to attach to, run:
byobu-select-session
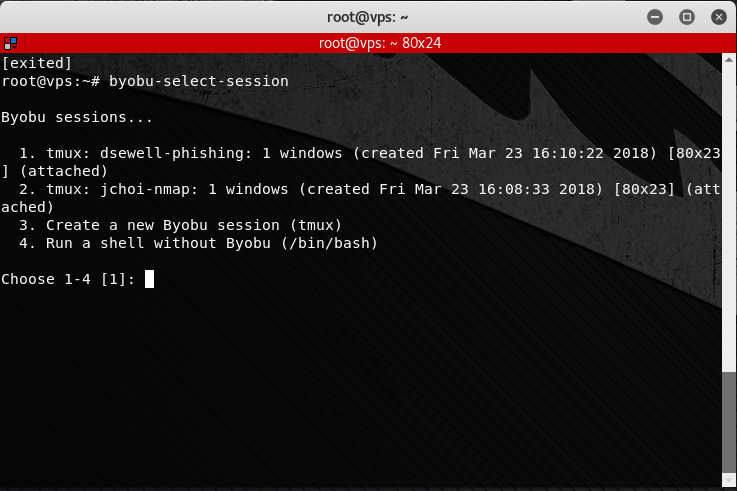
You will be presented with a list of currently running byobu sessions to attach to. Say, for instance, that we have created two sessions called “dsewell-phishing” and “jchoi-nmap” with the following commands:
byobu new -s dsewell-phishing
byobu new -s jchoi-nmap
When we enter “byobu-select-session”, we are presented with our list of sessions, as shown below:
If we select “1”, we are attached to the “dsewell-phishing” session. We and any other users attached to that byobu session will see all commands and output in that session. Remember, to exit the session leaving all terminals intact, type F6, not “exit”. “exit” will exit that terminal for all users attached to the session.
We can use byobu to help us with long running scans as follows.
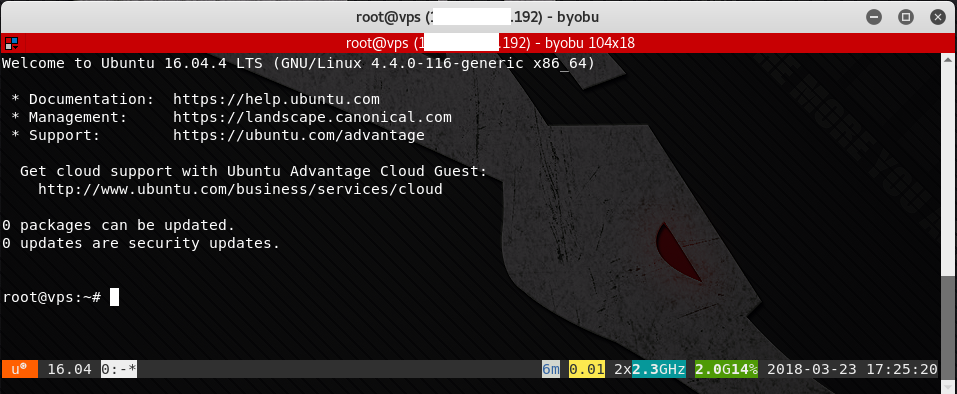
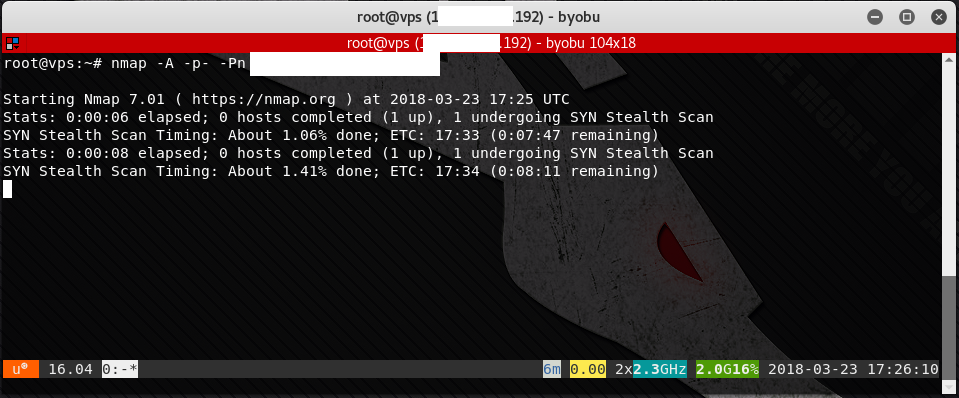
1. SSH into our Kali system with the fixed IP address. When connected, type byobu at the prompt. We will see the Message of the Day (motd) on the first session.
2. Launch the nmap scan. As we can see in the screen shot, the scan will take a few minutes. If scanning a large number of machines, or scanning through an Intrusion Detection / Prevention System (IDS/IPS), it could take many hours.
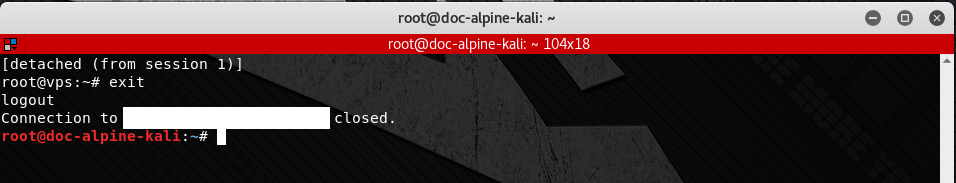
3. We can disconnect from the byobu session by hitting F6. After disconnecting from byobu, we can then type exit to end the SSH session. The byobu session, and all of its terminals, will continue running the background.
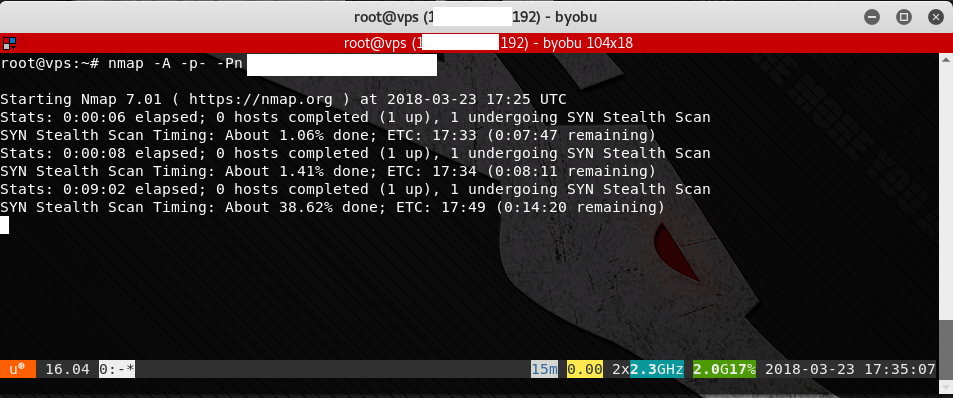
4. When we wish to continue, we can SSH back into our Kali system and type byobu (or if there might be multiple session running, type byobu-select-session). When we do, we are reconnected to byobu and all of its windows. We can see that the nmap scan has been continuing in the background, making further progress.
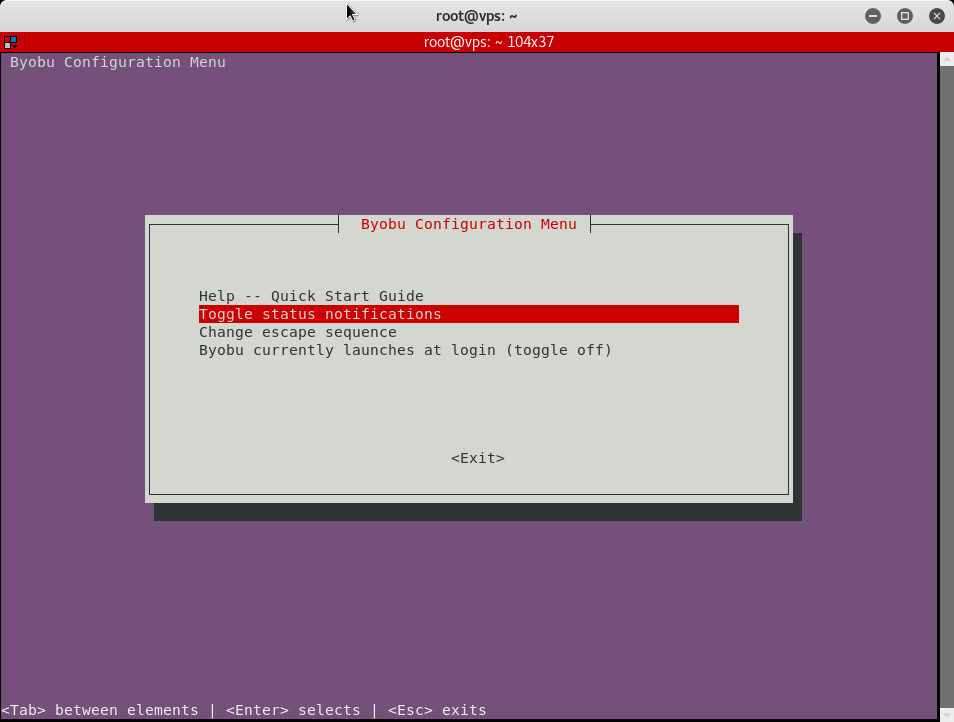
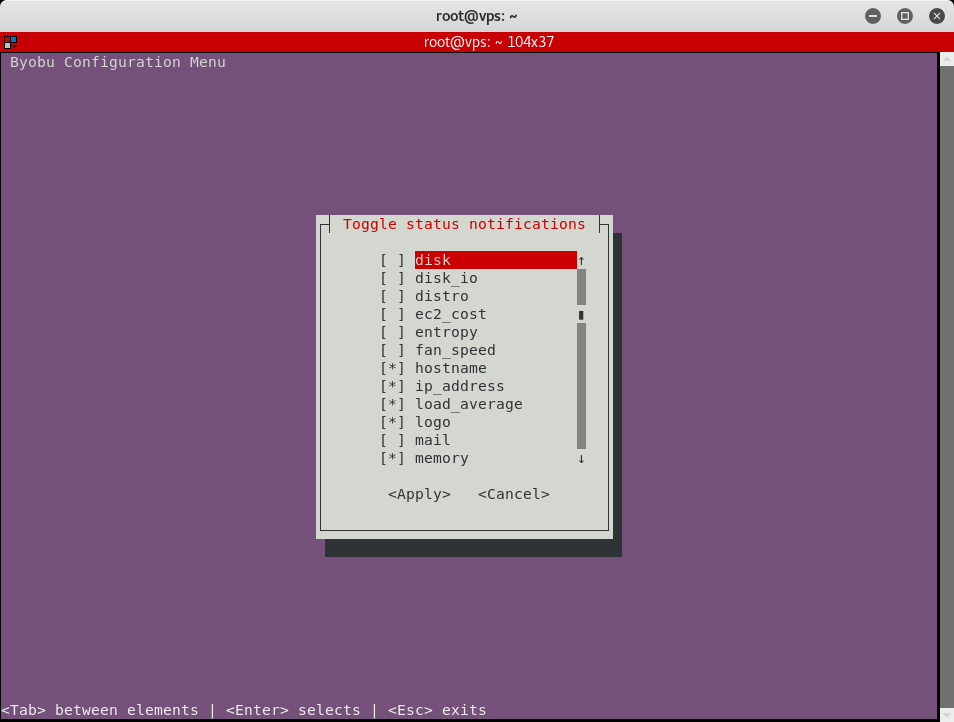
Byobu has some other cool features, such as the ability to customize the status bar at the bottom with the byobu-config program. Just run byobu-config (or simply hit F9 to open up the config utility in another byobu window) and select the status bar items you’d like to turn on or off. I find the IP address and hostname to be particularly useful.
You can also split a single window into multiple windows and navigate between them using the following commands:
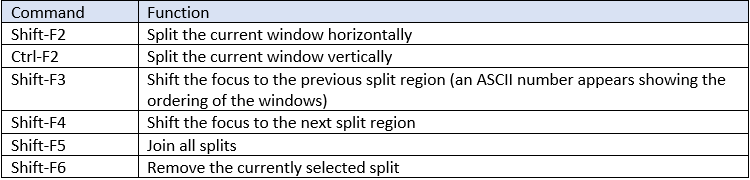
byobu command options
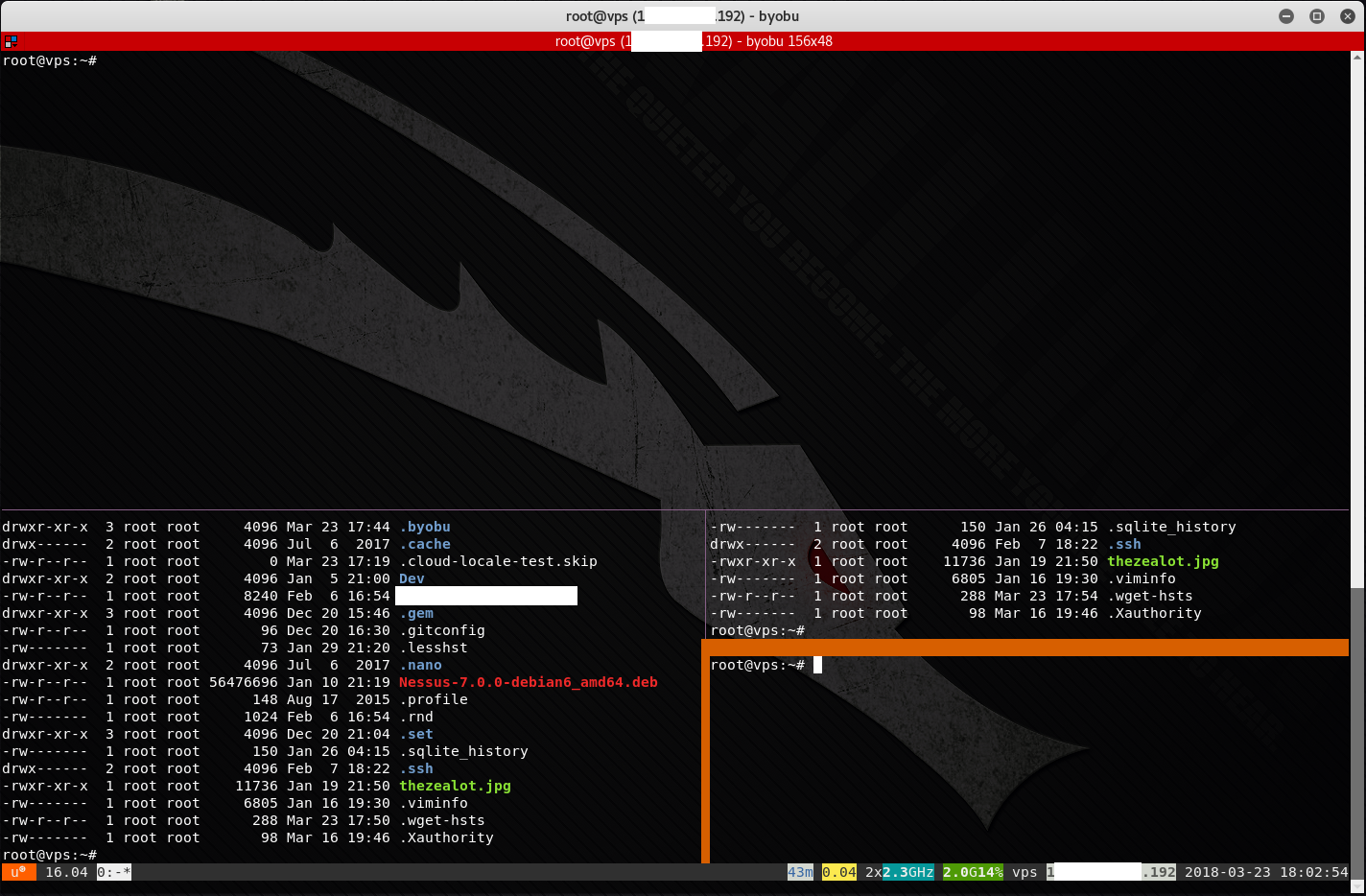
byobu with split windows
There are many more cool features in byobu. See the documentation webpage for details.
In my opinion, byobu is the best of the terminal multiplexers, because of its flexibility and its ease of use. It is an absolutely essential tool for managing Linux command-line operations that take a long time (and which must continue running even in the event of an accidental or intentional disconnect) and must be done over SSH.
Author Bio
Daniel “Doc” Sewell is the CTO and Trainer for Alpine Security. He currently holds many security-related certifications, including EC-Council Certified Security Analyst (ECSA), Licensed Penetration Tester (Master), Offensive Security Certified Professional (OSCP), Certified Information Systems Security Professional (CISSP) and Certified Secure Software Lifecycle Professional (CSSLP). Doc has many years of experience in software development, working on web interfaces, database applications, thick-client GUIs, battlefield simulation software, automated aircraft scheduling systems, embedded systems, and multi-threaded CPU and GPU applications. Doc’s cybersecurity experience includes penetration testing a fighter jet embedded system, penetration testing medical lab devices, creating phishing emails and fake web sites for social engineering engagements, and teaching security courses to world-renowned organizations such as Lockheed Martin and the Hong Kong Police Department. Doc’s hobbies and interests include home networking, operating systems, computer gaming, reading, movie watching, and traveling.