A cyber threat map, also known as a cyber attack map, is a real-time map of the computer security attacks that are going on at any given time. One of the most famous was released by the company Norse and went so viral, even among non-hackers, that it got its own story in Newsweek in 2015.
The map itself looks like a global game of laser tag. Beams of light, represented by different colors, shoot across a darkened screen showing where an attack comes from and where it is going. When it first caught the public eye, captivated audiences watched hackers wage cyber-war across hundreds and thousands of miles.
How Does A Cyber Threat Map Work?
If cyber attacks are sneaky mice – or, more appropriately, giant rats – then cyber attack maps work like the mousetrap.
Norse, for example, maintained a global threat intelligence network of more than 8 million sensors and “honeypots” in 47 countries across the world. These tools impersonated thousands of applications and devices that are common targets of hackers.
When a hacker hits a Norse sensor, the hacker believed that it had breached a system. Instead, Norse collected information about the hacker’s toolkit, including his or her IP address. This information then manifested as data on the cyber attack map.
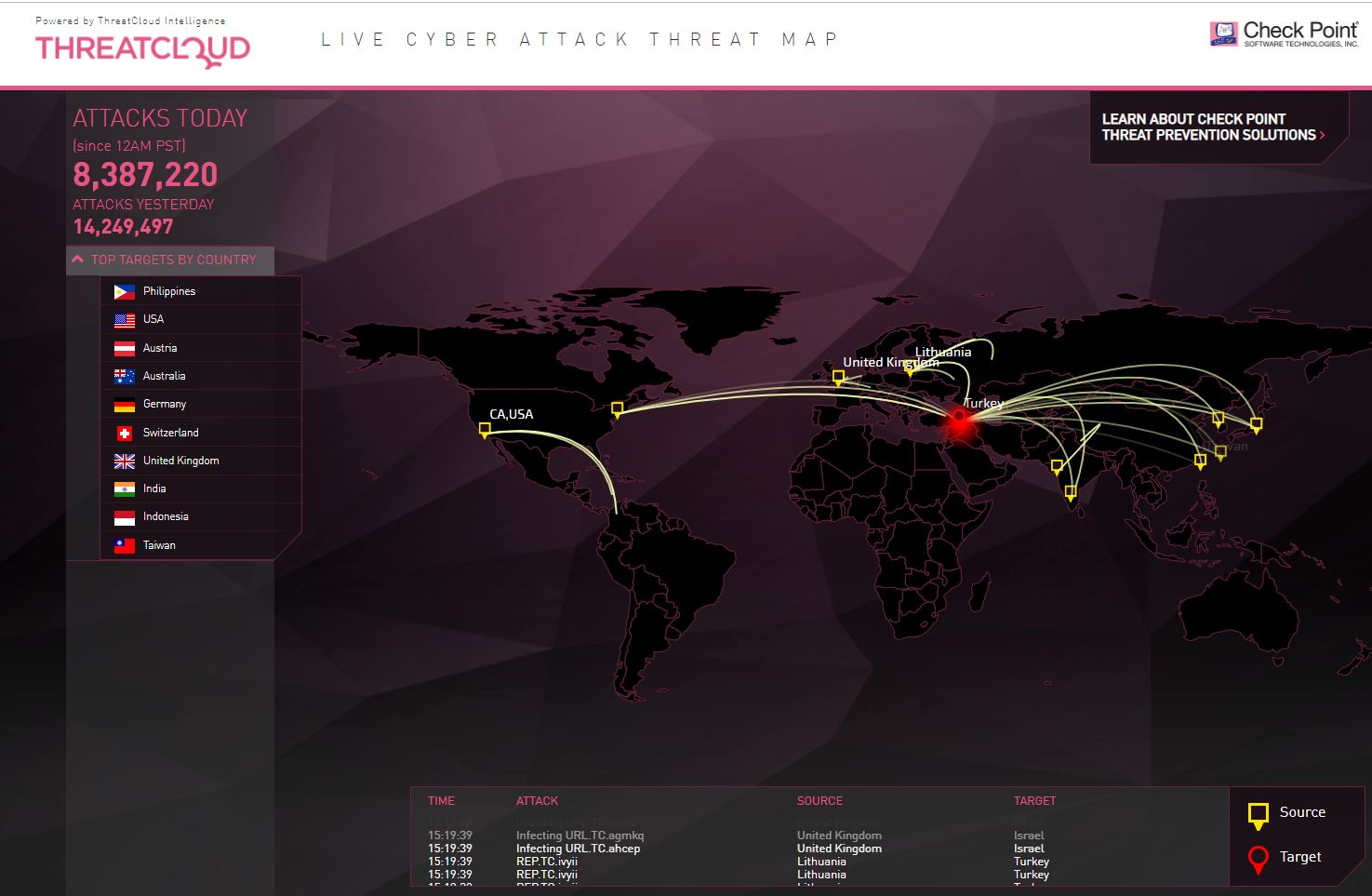
This model has continued past the demise of Norse to power live maps like Cyberthreat, ThreatCloud, and Fortinet. Some companies claim that these are real-time cyber attacks, but most are more like selections of recent attacks.
What Are They Good For?
First of all, anyone can look at a cyber threat map and understand something about current attacks. For laypeople, it might just be an understanding of how prevalent these attacks are.
For pros, a cyber threat map can provide data that can lead to the discovery of a potential new attack. Even though these maps don’t really show cyber attacks in real-time, they give you information, and a cybersecurity pro can never have too much of that.
The Best of the Best in Cyber Threat Maps
Not all cyber threat maps are created equal. Some are great eye candy for pen test companies, but others do offer good functionality. A few even let you manipulate the map to focus on its most useful information.
#1 Cyberthreat by Kaspersky Lab
Kaspersky’s cyber threat map may be the best in the business in terms of interactivity and visual appeal. It’s also mobile optimized so you can show it to clients or colleagues from anywhere. And if you want particular data, the site offers you the option to find it.
Narrowing It Down
Kaspersky’s Cyberthreat also offers useful statistics about current cyber attacks. Through its website, you can learn about:
-
Vulnerabilities identified
-
Most widespread threats
-
Botnet activity trends
-
Prevalence of infected mail and spam
You can find this data for a specific country or look at it on a worldwide level.
The Widget
Kaspersky Lab has figured out that cybersecurity professionals often use threat maps to visually represent their work to clients. To make it easier, they have created a Cyberthreat map widget, which you can embed in your website, as shown below, so that clients can see a representation of the latest threats.
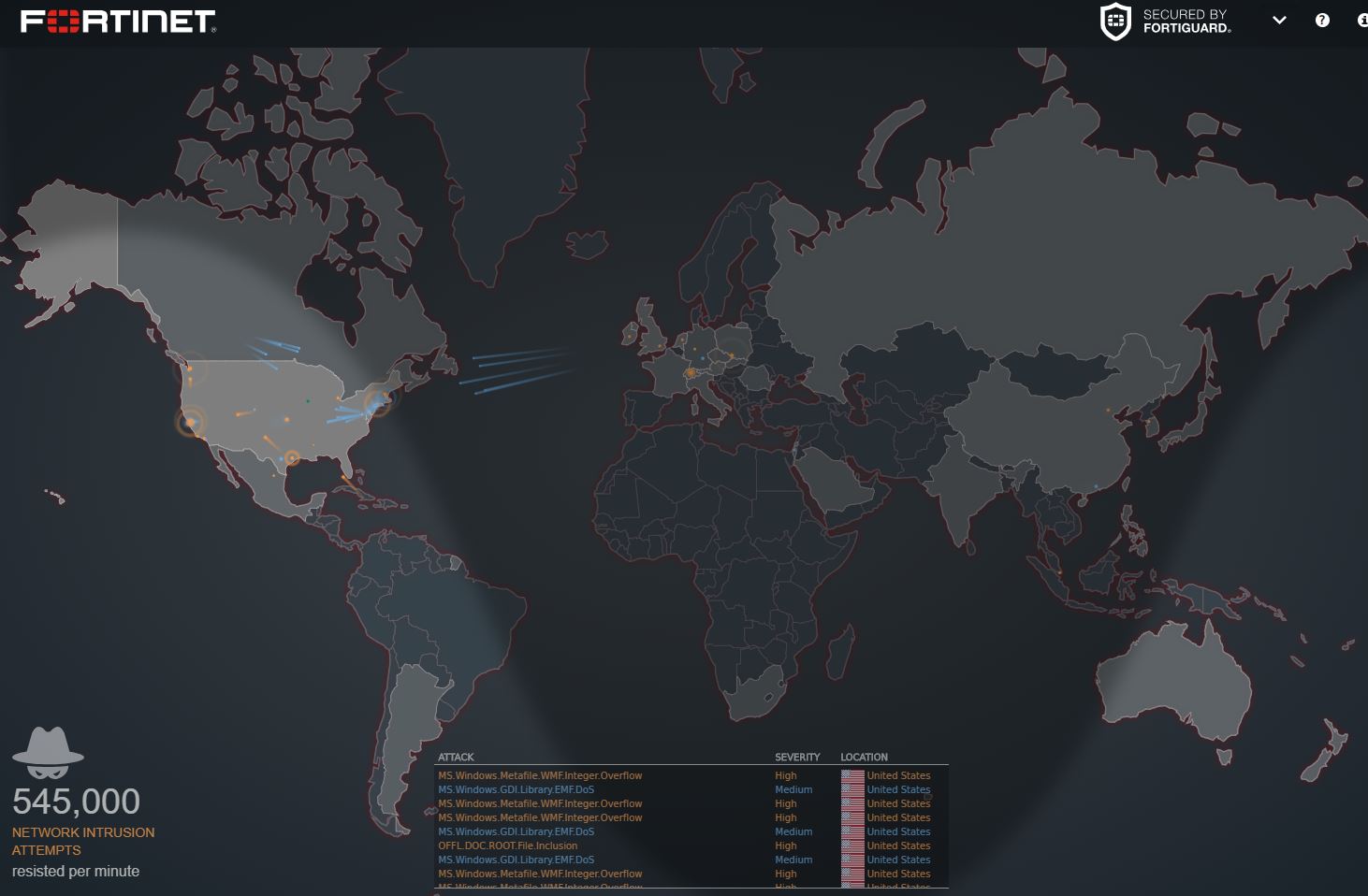
#2 Fortinet by Fortiguard
This one isn’t quite as customizable as Cyberthreat, but it’s informative enough to warrant runner-up honors. The main map color codes its attacks by severity to make it easier to focus on the most critical situations, coded in red. The details of these attacks scroll quickly along the bottom of the map, where the viewer can identify the threat type and location.
Fortiguard clients have a bit more freedom in terms of map design. By placing a tool known as the ThreatGate, users can monitor the threats approaching a particular location.
The Best of the Rest
In addition to Fortinet and Cyberthreat, there are a few other cyber attack maps that repeatedly appear on “Best of” lists. They are:
-
#4 FireEye
-
#5 Trend Micro
-
#6 Deteque
-
#8 Akamai
Each of these maps presents its data in a slightly different format and with a slightly different emphasis. Take a look, try them out, and find out which one will work best for you.
The Take-Away
If you find these maps intriguing, know that they’re not enough to make you an expert. You’ll need to learn more about cybersecurity and take some training, like the penetration testing courses available through Alpine Security. There are tests available for all levels of pen testers – check it out today.